Unlock full visibility of your external attack surface with DarkInvader’s continuous, real-time monitoring. Create your free account to discover unknown assets, detect emerging risks and stay ahead of potential threats before attackers can exploit them.
Create My Free Account
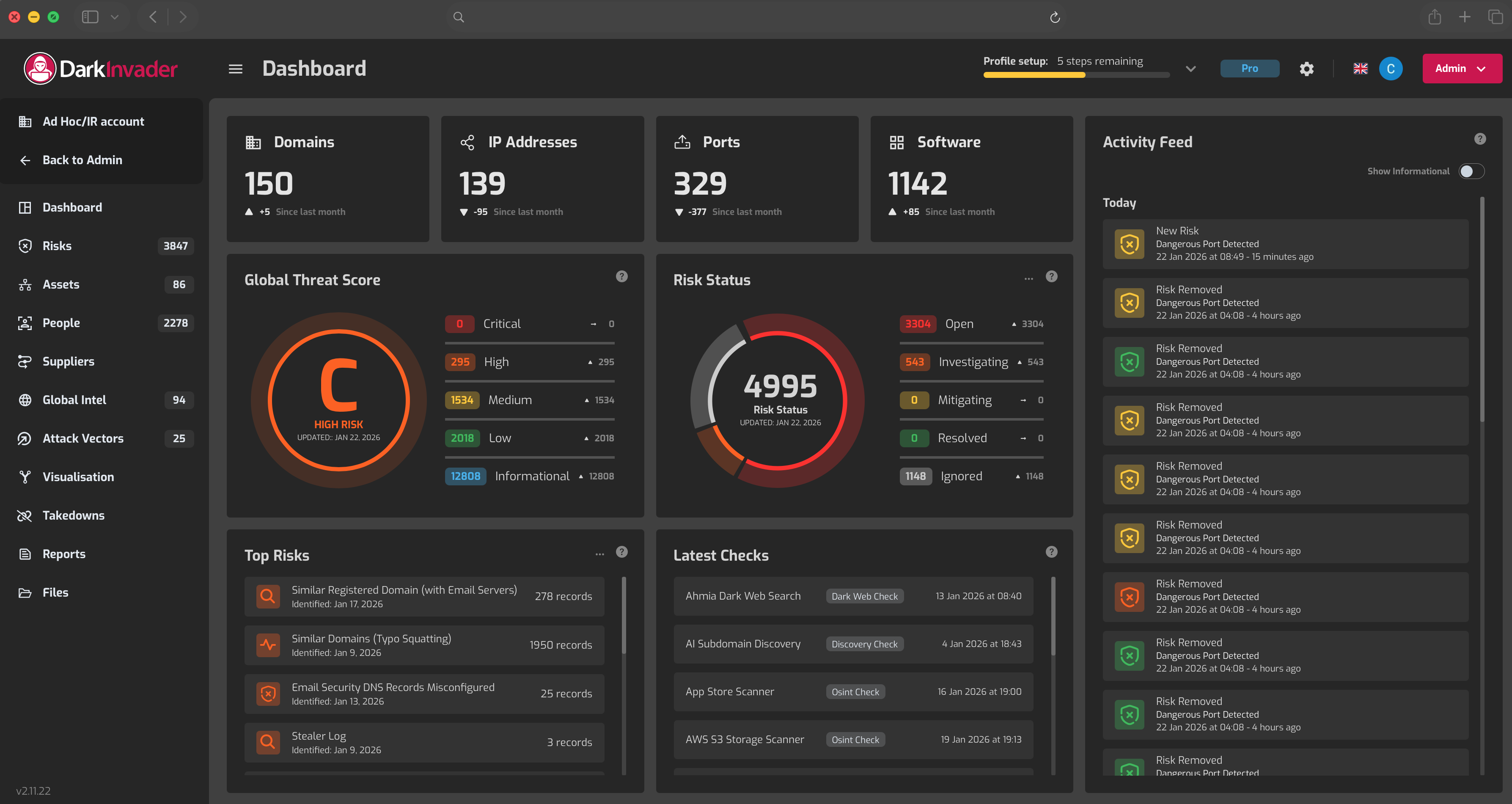
Achieve complete visibility of your external attack surface by automatically identifying every public facing asset across your digital footprint. The platform uncovers known and unknown components through continuous automated scanning, ensuring nothing is missed and establishing a strong foundation for reducing exposure and improving security posture.
DarkInvader performs comprehensive external asset discovery to identify every internet-facing component associated with your organisation. This includes domains, subdomains, IP addresses, cloud services, SaaS platforms, APIs, and externally exposed systems. By continuously mapping your digital footprint beyond what is formally documented, we ensure no publicly reachable asset is overlooked. This gives security teams a complete, real-world view of what attackers can see and target, not just what internal records suggest exists.
All discovered assets are presented through clear, structured visual mapping, allowing teams to understand their external attack surface at a glance. Relationships between domains, infrastructure, cloud providers, and services are made explicit, helping security, IT, and leadership teams quickly assess complexity and risk. This visual clarity supports faster decision-making, prioritisation of remediation efforts, and more effective communication between technical and non-technical stakeholders.
DarkInvader actively identifies shadow IT, legacy systems, and forgotten infrastructure that often sit outside formal governance and security controls. These assets frequently arise from historic projects, third-party vendors, rapid cloud adoption, or unmanaged SaaS usage. By uncovering systems that are unknown, unmanaged, or no longer maintained, DarkInvader helps reduce hidden risk that would otherwise remain invisible until exploited.
DarkInvader provides geographical mapping of your internet-facing assets, showing where infrastructure is hosted across regions, countries, and cloud environments. This visibility supports compliance, data residency awareness, and third-party risk management, while also highlighting unexpected or high-risk hosting locations. Understanding the geographic distribution of assets helps organisations assess jurisdictional exposure, supply chain dependencies, and potential attack paths more effectively.

Maintain a clear view of evolving risks by continuously monitoring your public facing assets for configuration changes, new exposures and emerging vulnerabilities. This ongoing oversight ensures that potential threats are identified early, allowing security teams to respond quickly and reduce external attack surface risk.
DarkInvader continuously monitors your external attack surface to detect changes as they happen. This includes new domains, subdomains, IP addresses, services, cloud resources, and configuration shifts that introduce fresh exposure. As organisations evolve, assets are frequently added, modified, or removed without full visibility. Continuous detection ensures security teams are immediately aware of newly exposed entry points, rather than discovering them after an incident has occurred.
Not all external exposures present the same level of risk. DarkInvader applies intelligent prioritisation to highlight the assets and vulnerabilities most likely to be exploited. By assessing factors such as asset criticality, exposure level, configuration weaknesses, and attacker relevance, teams can focus remediation efforts where they matter most. This reduces alert fatigue and allows security resources to be allocated efficiently to the highest-impact risks.
DarkInvader maintains a historical record of changes across your external assets, providing clear visibility into how your attack surface has evolved over time. This includes when assets were introduced, modified, or decommissioned, and how exposure levels have shifted as a result. Historical tracking supports incident investigations, compliance reporting, and internal audits, while also helping organisations identify patterns that lead to recurring risk.
When critical changes or high-risk exposures are detected, DarkInvader delivers real-time alerts and notifications to ensure rapid response. Alerts can be tailored to severity, asset type, or risk category, enabling teams to act before attackers do. This proactive approach reduces dwell time, supports continuous security operations, and ensures emerging threats are addressed as soon as they appear in the external environment.
Discover the impact of real-time, continuous security monitoring with DarkInvader Book a demo today and learn how to take full control of your external attack surface.
Schedule My Demo
The Assessment stage in DarkInvader scans both infrastructure and web applications to identify high risk vulnerabilities across your external attack surface. By modelling realistic attack behaviours, it helps your team prioritise the issues that matter most and address them efficiently. Combined with continuous monitoring and clear, actionable insights, it supports a more secure and resilient environment against evolving threats.
DarkInvader uses a dual engine vulnerability scanning approach to identify security weaknesses across your external attack surface. By combining automated scanning with complementary detection techniques, DarkInvader increases coverage and accuracy while reducing false positives. This layered methodology enables the identification of common vulnerabilities, misconfigurations, and emerging exposures that single-engine scanners often miss, providing a more reliable view of external risk.
Once vulnerabilities are identified, DarkInvader automatically tracks their resolution status over time. As assets are patched, removed, or reconfigured, the platform validates whether issues have been successfully remediated or if exposure remains. This continuous verification helps security teams demonstrate progress, avoid duplicate work, and maintain confidence that fixes have genuinely reduced risk rather than simply appearing resolved in internal ticketing systems.
DarkInvader delivers detailed, actionable vulnerability reporting designed for both technical and executive audiences. Each finding is clearly explained with context around risk, potential impact, and recommended remediation steps. Reports are structured to support rapid triage, prioritisation, and compliance requirements, enabling teams to move from discovery to remediation without ambiguity or unnecessary investigation.

The Intelligence stage of DarkInvader provides in depth visibility of external threats by analysing OSINT from both the surface and dark web. Using AI to detect patterns, exposures and emerging risks, it highlights exploitable vulnerabilities and identifies threats that target high risk individuals. With dedicated VIP monitoring, DarkInvader helps protect sensitive staff and critical assets from evolving external threats.
• Proprietary Dark Web Crawler
• AI Powered Stealer Log Analysis
• AI Powered Content Analysis
• Coverage of key Channels
• Keyword and Identifier Detection
• Real-Time Alerts and Reporting
• Proprietary Darchive Database
• AI-Powered Deduplication
• Leaked Credential Alerts
• Flexible Incident Management
• Detailed Record Information
• Automated Intelligence
• Proactive Domain Surveillance
• Available Domain Detection
• Actionable Insights
• Supplier Threat Intelligence
• Accreditation Tracking
• Supplier Threat Scoring
• Contextual Intel Matching
• Four Core Focus Areas
• Exportable Reports and IOCs
• Aggregated Threat Intelligence
• Internal vs External Identites
• VIP Tagging and Alerts
Submit your domain to DarkInvader and uncover any exposed data on the Dark Web. Stay ahead of threats by discovering vulnerabilities before attackers do—completely free.
Get My Free Scan
The Mitigation stage in DarkInvader supports swift and coordinated action on the risks identified during discovery and assessment. It goes beyond highlighting vulnerabilities by providing clear remediation steps, tracking progress and validating completion. With an intuitive record status driven interface, your team can reduce the external attack surface systematically and strengthen overall security posture.
DarkInvader provides a full end-to-end website takedown service to disrupt malicious infrastructure targeting your organisation. This includes phishing sites, impersonation domains, fraudulent portals, and unauthorised brand misuse. From initial discovery and validation through to takedown execution and confirmation, DarkInvader manages the entire process. This removes operational burden from internal teams and ensures malicious content is addressed quickly, consistently, and professionally.
Effective takedowns require clear, verifiable evidence. DarkInvader conducts thorough evidence collection to support takedown requests, capturing page content, hosting details, DNS records, SSL information, and relevant indicators of abuse. All evidence is documented in a structured and defensible manner, supporting registrar, hosting provider, and platform requirements. This approach increases takedown success rates and provides a clear audit trail for internal reporting or legal review.
DarkInvader handles direct communication with domain registrars, hosting providers, and relevant service operators on your behalf. Takedown requests are submitted using accurate technical detail and appropriate abuse channels to accelerate response times. By managing registrar engagement end to end, DarkInvader ensures consistent messaging, reduces delays caused by incomplete submissions, and improves the likelihood of swift action against malicious infrastructure.

The Reporting stage in DarkInvader enables the creation of clear, structured reports that summarise your external security posture and track key changes over time. Management Summaries, What’s Changed reports and VIP Profiles provide focused insight into your public facing assets and emerging risks. Reports can be generated on demand or scheduled for automated email delivery, giving your team flexible oversight of security progress.
DarkInvader delivers clear, structured management reports that translate complex external risk data into meaningful insight for leadership teams. Reports are designed to support informed decision-making, demonstrate security posture, and track progress over time. By presenting external threat and exposure data in a concise, executive-friendly format, DarkInvader helps organisations align security activity with business risk and governance objectives.
What’s Changed reports provide a focused view of how your external attack surface has evolved since the previous reporting period. These reports highlight newly discovered assets, removed infrastructure, emerging exposures, resolved issues, and shifts in overall risk profile. By clearly showing change over time, security leaders can quickly understand what requires attention, justify remediation efforts, and communicate impact to stakeholders without needing to interpret raw technical data.
VIP Profile reports focus on individuals at heightened risk, such as executives, board members, and high-profile staff. DarkInvader assesses external exposure related to these profiles, including impersonation risks, leaked credentials, and targeted infrastructure misuse. These reports support executive protection, brand trust, and reputational risk management by providing tailored insight into threats that specifically affect high-value individuals within the organisation.
• Real-Time Alerts
• Email Notifications
• Support for Slack, Jira, and more
• Multiple API Key Management
• Real-Time Data Access
• Simple, Secure Access